Achieving CIS Critical Security Controls 1 & 2 in Asset Management
Blog

Table of Contents
Take Control of Your Assets
A personalized demo is just one click away.
Modern IT organizations face an ever-evolving threat landscape, and the CIS Critical Security Controls framework provides a prioritized set of best practices to reduce risk. The first two controls – Inventory and Control of Enterprise Assets and Inventory and Control of Software Assets – are especially foundational, focusing on knowing exactly what assets you have and ensuring they are secured. By implementing these controls, IT teams can shrink their attack surface, prevent unknown devices or applications from lurking in the network, and maintain compliance with industry standards.
Understanding CIS Critical Security Controls
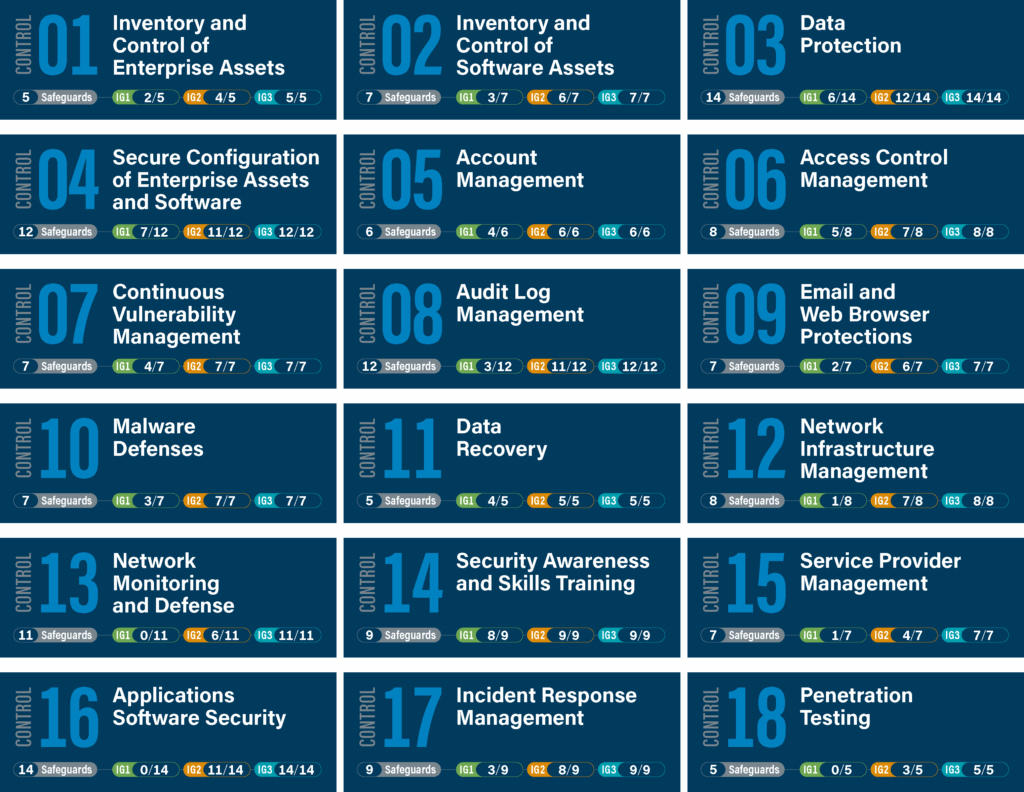
The CIS Critical Security Controls are 18 best-practice measures developed by the Center for Internet Security to help organizations prioritize their cybersecurity efforts. Controls 1 and 2 form the core foundation of this framework, both dealing with asset management. Essentially, these two controls focus on knowing exactly what hardware and software your organization has, and making sure only authorized assets are present in your environment.
CIS also divides these controls into three Implementation Groups (IG1, IG2, IG3) to guide adoption. Controls 1 and 2 fall under IG1, the category of essential cyber hygiene. That makes them a top priority as they yield significant risk reduction and are recommended for all organizations as a starting point.
CIS Control 1: Inventory and Control of Enterprise Assets
What it is: Control 1 requires actively managing all enterprise hardware assets. In simple terms, your IT team must know about every device that connects to your network, from servers, PCs and laptops to network equipment, IoT devices, and even employee-owned devices if they access company data. Maintaining a reliable, up-to-date inventory of these assets is crucial. This control also means ensuring only authorized devices are allowed on the network and swiftly identifying/removing any unauthorized device.
Why it matters: If you don't know a device exists, you can't protect it. Untracked hardware becomes a blind spot that attackers can exploit. For example, an employee plugging in an unapproved router or a forgotten laptop could quietly introduce vulnerabilities. Implementing Control 1 closes these gaps and ensures every connected asset meets your security standards.
Implementing CIS Control 1 (Hardware Asset Management)
Here are key practices for implementing Control 1 effectively:
1. Build a complete asset inventory
Catalog every device that connects to your IT environment. Include servers, computers, mobile devices, networking gear, IoT gadgets, etc. Assign each asset a unique identifier and record details (e.g., owner, location, network addresses, etc.).
2. Control network access
Only allow approved devices to connect. Set up a process to authorize and register new hardware before it joins the network, and label or tag equipment once approved. Use network monitoring or access control tools (e.g., NAC) to automatically detect and block any device that isn’t in your inventory until it is verified.
3. Audit the inventory regularly
Keep the asset list current. Conduct periodic audits (for example, quarterly or annually) to verify the inventory’s accuracy. Remove or update entries when devices are decommissioned or changed. Regular audits ensure you maintain an accurate picture of your hardware at all times.
4. Leverage automation tools
Use IT asset management software (like Asset Panda) to automate inventory tracking. These tools can automatically discover new devices on the network, alert you to changes, and maintain an audit trail of assets. Automation reduces manual effort and helps enforce Control 1 consistently.
Following these steps will fulfill the requirements of Control 1. The result is full visibility into all hardware assets, so your security team can manage device configurations, deploy patches, and respond to threats with confidence that no device is off the radar.
CIS Control 2: Inventory and Control of Software Assets
What it is: Control 2 focuses on knowing and managing all software in your environment so that only authorized software is installed and running. This means keeping an inventory of all software and operating system versions on each device. Your organization should have a clear record of what software is present on every system, ensure those applications are approved and up-to-date, and swiftly address any software that shouldn’t be there.
Why it matters: Unmanaged software is a serious security risk because outdated or unauthorized applications can become gateways for attackers. Implementing Control 2 gives IT teams visibility into all software running in the company, making it easier to spot missing patches or unsafe programs and to verify that software is properly licensed. This control helps avoid compliance issues by preventing unlicensed or unsupported software from lingering in your environment.
Implementing CIS Control 2 (Software Asset Management)
Key practices for implementing Control 2 include:
1. Maintain a software inventory
Catalog all software (operating systems and applications) installed on each device, along with version numbers and how many installations or licenses are in use. Automated discovery tools or endpoint management systems can help keep this list accurate and up-to-date.
2. Enforce allowed software
Define which software (and specific versions) are approved for use in your organization. Implement policies and technical controls to prevent installation or execution of anything outside this approved list. For example, you might use application allowlisting or restrict administrator privileges to block unapproved software.
3. Keep software updated
Ensure all software in your inventory is routinely updated with the latest security patches. An accurate inventory lets you quickly identify which systems need patching when new vulnerabilities are disclosed. Prompt updates close known security holes and significantly reduce the risk of compromise.
4. Audit and remove unwanted software
Periodically review systems for software that is not authorized or no longer needed and uninstall any such applications. This cleanup removes potential vulnerabilities and helps maintain a lean, secure software environment. Continuous auditing prevents "software creep" from undermining your security over time.
By diligently managing software assets in this way, your organization will satisfy Control 2. You'll reduce the attack surface by eliminating risky or unapproved programs and ensure that all essential software is properly maintained and licensed.
Conclusion: Asset Management as the Foundation
The first two controls in the CIS framework are all about having complete visibility and control over your technology assets. Once CIS Critical Security Controls 1 and 2 are in place, you have a solid foundation – you can't defend what you don't know about, and these controls make sure you know exactly what's in your environment. With a complete inventory of hardware and software, all other security measures become more effective.
Using the right tools can greatly streamline this process. Asset Panda is an IT asset management platform that centralizes your asset inventory and automates many tracking tasks like discovering new devices and logging software changes. By leveraging Asset Panda, your team can save time and ensure asset records stay accurate, making it much easier to uphold Controls 1 and 2.
Focusing on Controls 1 and 2 is a smart strategy for any security-conscious organization. Managing your assets with discipline – and with help from a solution like Asset Panda – will ensure you fulfill CIS Critical Security Controls 1 and 2 while strengthening your overall cybersecurity posture.
Request your demo to see how Asset Panda can streamline your asset tracking and help you comply with CIS Controls 1 and 2.
Take Control of Your Assets
A personalized demo is just one click away.
Related News & Press
Learn more from a solution specialist
Schedule a demo to find out how you can transform your workflows with Asset Panda Pro
Contact our team at (888) 928-6112